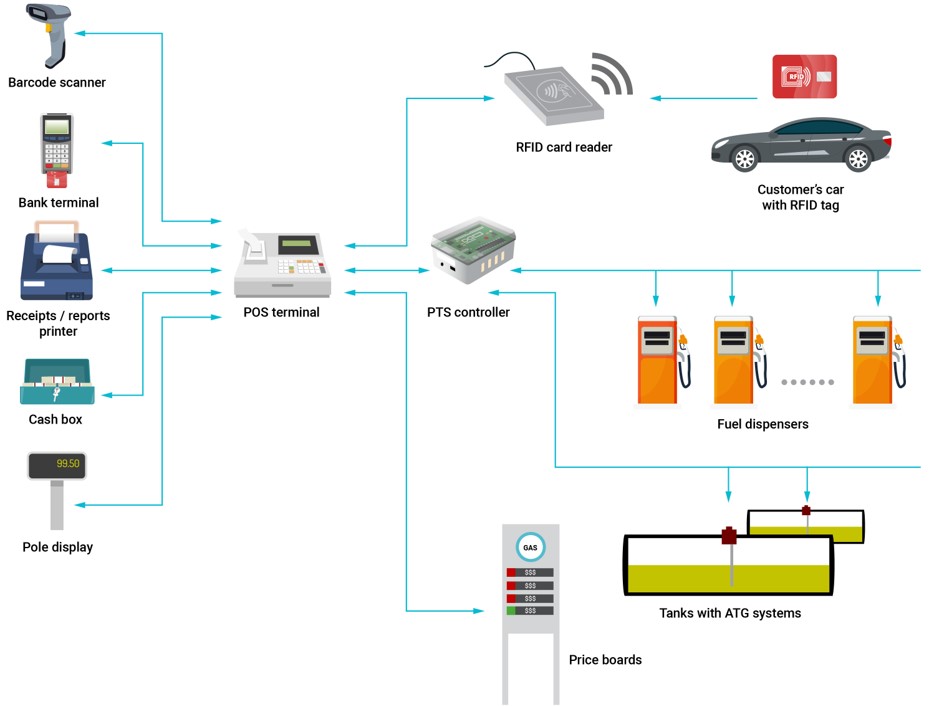
Gas station security
Verizon’s 2019 Data Breach Investigations Report analyzed 2,013 data breaches and found that 69% were perpetrated by outsiders while 34% included the involvement of internal actors (1).
Internal issues are a result of weak security policies or user passwords, downloading unwanted software, or disgruntled employees. External security threats often come from state or criminal organizations, hacktivists or simply hackers with a desire to disrupt. Typically, hackers want to gain control of an environment in order to disrupt business processes, hold an organization hostage, hide their trails through a company network, or gain access to a bigger prize on the network.
Anatomy of a cyber attack
Usually a hacker attack occurs in a specific order where the hacker researches their target, finds a vulnerability to exploit and then expands the attack to other equipment within the network as they look for something of value. When a hacker is researching an attack, they are gathering public information like network ranges, MAC/IP addresses, domains or host names, and they will likely use IP scanning software to find their targets. They will then use the information gathered on the network by pairing it with known vulnerabilities and breach the network security. Once in, they will look for other equipment that will support gaining access to other valuable devices or data on the network. Depending on their intent, the value that a hacker is after may be a pattern of operation, access to other systems, credit card data, passwords, or ransom.
Protecting your network from intrusion
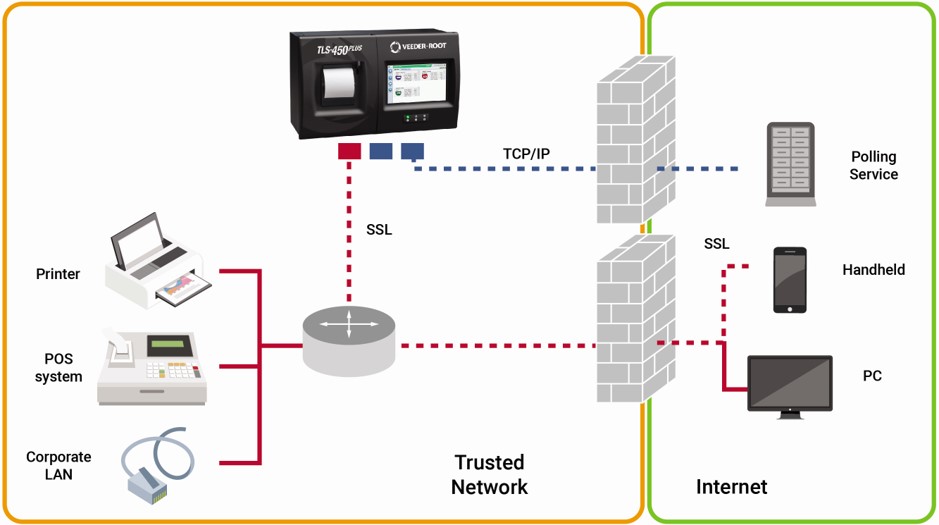
The best way to protect your gas station or fueling site from unwanted access is to have a detailed corporate security policy in place that incorporates the advanced features of the TLS-450PLUS Automatic Tank Gauge (ATG). This includes using a firewall as the first line of defense in your network, like the Cisco® RV042 Dual WAN VPN Router (2) (P/N: 330020-818) offered through Veeder-Root. You will also want to ensure that you are separating your traffic. PCI compliant data should be kept separate from other data, including tank gauge data which is not governed by the Payment Card Industry Security Standards Council.
Veeder-Root routinely updates the software for its TLS-450PLUS ATG and each release includes patches and updates for any recently identified vulnerabilities. It is best practice to periodically update console software. It is also important for automatic tank gauge users to create an administrator account on the gauge and use custom user rules to determine which users will receive access to critical fuel site data.
Network connections
The network connection to the TLS-450PLUS ATG can be managed through the three ethernet ports for either a direct connection or through an internal switch. Port numbers can be reassigned to use non-standard numbering and MAC/IP addresses filtering should be used as well; both of steps make it harder for hackers to identify access points. Any port that is going unused should be disabled, and if using a 10001-Serial port you should use encrypted data (SSH – Secure SHell) instead of using a plain text interface. It’s also recommended that routing tables are used to limit access and route data.
To protect your data, it is important that you have a security policy in place that meets your organization’s needs and that you have trained staff to be aware of issues. If there is a security breach, your team needs to learn from it, periodically update policies and continue to improve by implementing a security feedback loop.
(1) 2019 Verizon Data Breach Investigations Report. https://enterprise.verizon.com/resources/reports/dbir/
(2) Cisco® RV042 Dual WAN VPN Router is a registered trademark of Cisco Systems, Inc. and/or its affiliates in the United States and certain other countries.
Webinar Replay: Protecting Gas Station and Fuel Site Data
View this webinar replay to hear our full discussion of data security as it relates to gas stations and our TLS-450PLUS automatic tank gauge and best practices for maintaining a secure network.
View the full webinar